Importance of 2FA in the current world
Gone are the days when gathering information, exchanging ideas, and doing business were a huge hassle. With the availability of the internet, everything has become easily available to us. This not only saves time but helps reach our message to a wider public. Although usage of the internet has become very easy, it is associated with many risks. Whether you are a small business, an institute, a college student, an employee, or any other organization. It is important that the information we store online is safe and secured. Despite having security options, there are still many cases where data theft has happened. Accounts of many important people have been hacked, so common people like us cannot be assured that our data is safe online. So what is the solution? Should we stop being online? Impossible right? Since there is no turning back now, we hope for better security options to be made in the future. But as of now, the option available to us is 2FA i.e 2 Factor Authentication. In SFA or Single Factor Authentication, the user is asked for a username and password. 2FA is an extra security step that a user is asked to prove his/her identity online. This ensures that the person accessing the account or information belongs to them or is permitted to them. 2FA methods can be different for various applications. Some applications ask to save information of friends in case of recovery of the account. This way, in case of identity theft these alternative users also get notified. There are cases where applications and accounts with 2FA enabled have also been hacked. In order to be on the safe side, the least we can do is follow all the available preventive measures.
Cases of data breach - In the News
In 2020, many prominent US figures such as Elon Musk, Jeff Bezos, Bill Gates, Barack Obama, Joe Biden, and Kanye West’s Twitter account were hacked in the Bitcoin Scam. Again in 2020, records of 10 million guests were exposed due to a data breach in MGM resort of Las Vegas. In April 2020, it was found that hackers stole zoom passwords and sold them on the dark web. They did this through credential stuffing and the accounts that were successfully compromised were packaged to a new database.
If that happened to them, how much more likely is it to happen to us? Give it a thought!
Few hacking techniques used by Cybercriminals
Hackers must be having millions of techniques to steal data. Below are a few commonly known methods and ways to prevent data theft.
Application Updates - Users usually don’t consider updating applications to be a necessary action. Application updates usually come with security patches that help to protect our systems. When applications are not updated, it becomes easy for the hacker to steal your data. Hence, it is advised to update your applications regularly.
USB Hacking - Hacking via USB Sticks is another way used by cyber thieves. You just have to plug in the USB to your computer and he will succeed in trapping you into a ransomware attack. In a recent case, USB Sticks containing malware were being sent to US Companies in the name of presents. These hackers were a group called FIN7, who made these presents look authentic and hence tempted the employees to take them. One way to avoid being a victim of identity theft is to think twice before taking and plugging any such USB into your personal or work-related data containing device.
Unsafe Sites - Cookies used in your websites store personal information and hence when you access a non-secure website, you are prone to risk your data. Google sends a warning message and asks users to return back to safety while entering an unsafe website. An HTTPS website ensures security and websites with only HTTP mean it is not secured. These are only a few from the millions of possibilities. As a result, every internet user needs to be aware of online data security.
The Solution
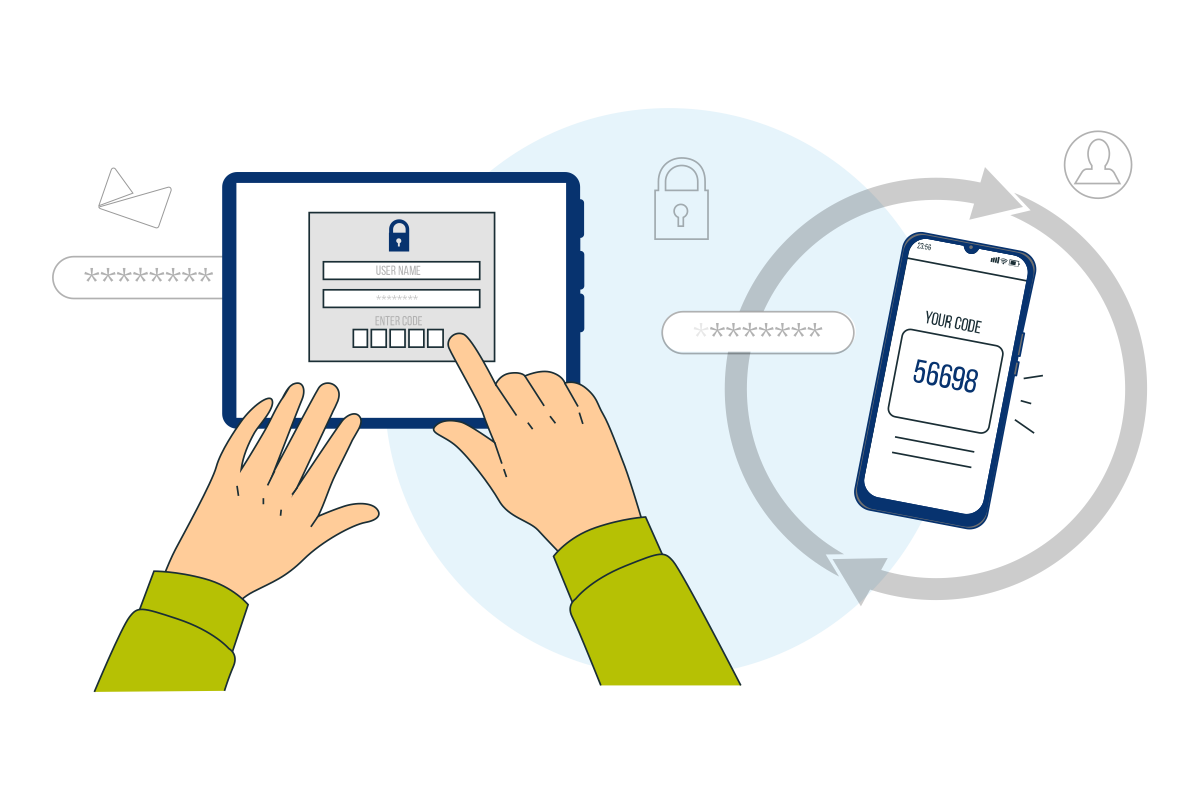
Authentication is necessary to ensure that we have permission to access the content. We have SFA i.e Single Factor Authentication and 2FA i.e Double Factor Authentication. As previously stated, SFA does not provide the same level of protection as 2FA. This is because 2FA adds an additional layer of protection including the ordinary method. This additional security step could be sending a one-time password to your phone/email, biometrics using your face or finger. Other methods of 2FA include authentication via hardware using a key fob or dongle. This is considered one of the most secure 2FA methods and is commonly used for businesses. The hardware method does not require an internet connection as it comes with an LCD screen and at every 30-60 seconds, a new code is displayed. Although this method provides double security, it is important to understand the fact that nothing is completely secure.
ust like your browser, it is necessary to protect your emails if you have an online presence. If you have ever noticed, any social media application or bank account you own, all the recovery passwords are sent to the email. If the cybercriminal has your email hacked, he is obviously going to hack all these other accounts easily. As a result, it’s critical that you keep your email secure. Ask your email provider if there is 2FA available for your email solution. Now as you know the importance of 2FA, next time make sure that you are using a safe online platform. Although with 2FA, safety is not 100% guaranteed, it is better to be not reliable on SFA. Why take risks when you have the option to have better security?
When it comes to data security, ENTP Mail is a reliable platform. With 2-factor authentication, a dedicated team of professionals also provides 24/7 tech support in case of any assistance required.